A threat actor has quietly spent the last two years integrating into the core team of maintainers of XZ Utils, a freeware command-line data compressor widely used on Linux systems. The attacker slowly managed to integrate a backdoor into the software that was designed to interfere with SSHD and allow remote code execution via an SSH login certificate. The backdoor was discovered a few days before being released on several Linux systems around the world.
The threat actor is suspected to be a developer by or using the name Jian Tan. Several security experts believe this supply chain attack could be state-sponsored.
What is XZ Utils and what is XZ Backdoor?
XZ Utils and its underlying library liblzma is a free software tool that implements XZ and LZMA, which are two compression/decompression algorithms widely used on Unix-based systems, including Linux systems. Many operations on those systems use XZ Utils to compress and decompress data.
He CVE-2024-3094 The backdoor found in XZ Utils was implemented to interfere with authentication in SSHD, the OpenSSH server software that handles SSH connections. The backdoor allowed an attacker to execute remote code via an SSH login certificate. Only XZ Utils versions 5.6.0 and 5.6.1 are affected.
How the XZ Backdoor Was Cautiously Implemented for Over Years
On March 29, 2024, software engineer at Microsoft. Andrés Freund reported the discovery of the back door. He found it when he became interested in the strange behavior of a Debian sid installation, such as SSH logins consuming a lot of CPU and electoral gate errors and decided to analyze the symptoms in depth. Freund explained that the discovery of the backdoor in XZ was lucksince it “really required a lot of matching.”
However, it seems that the implementation of the backdoor has been a very quiet process that lasted about two years. In 2021, a developer named Jian Tan, username JiaT75, appeared out of nowhere to start working on the code for XZ Utils, which is not unusual because free software developers often work together to update code. Tan has frequently contributed to the XZ project since late 2021, slowly building trust in the community.
In May 2022, an unknown user used a fake name Dennis Ens complained on the XZ mailing list that the software update was not successful. Another unknown user, Jigar Kumar, entered the discussion. two times to pressure XZ Utils lead developer Lasse Collin to add a maintainer to the project. “Progress will not happen until there is a new leader,” Jigar Kumar wrote. “Why wait until 5.4.0 to change maintainers? Why delay what your repository needs?
Meanwhile, Collin voiced that “Jia Tan has helped me get off the list with XZ Utils and could have a bigger role in the future, at least with XZ Utils. It is clear that my resources are too limited (hence the large number of emails waiting for a response), so something has to change in the long term.” (Collin wrote Jia in his message, while other messages reference Jian. To add to the confusion, Jian's nickname is JiaT75.)
In the following months, Tan became increasingly involved in XZ Utils and became a co-maintainer of the project. In February 2024, Tan issued commits for XZ Utils versions 5.6.0 and 5.6.1, both of which contained the backdoor.
It is also interesting to note that in July 2023, Tan requested to disable ifunc (GNU indirect function) in oss-fuzz, a public tool created to detect software vulnerabilities. That operation was likely performed to allow the backdoor in XZ to go undetected once it was launched, as the backdoor makes use of that feature to achieve its goals.
Finally, the attacker has contacted several people responsible for different Linux distributions to include the backdoored versions of XZ Utils in their own distributions. RedHat's Richard WM Jones wrote about this on a forum: “Very upset – the apparent backdoor author was in communication with me for several weeks trying to add xz 5.6.x to Fedora 40 and 41 because of its 'great new features'. We even worked with him to fix the valgrind issue (which now turns out to have been caused by the backdoor he had added). Last night we had to race to fix the problem after an involuntary embargo break. He has been part of the xz project for 2 years, adding all sorts of test binaries and to be honest, with this level of sophistication I would be suspicious of even older versions of xz until proven otherwise.” Tan also tried to include it in Ubuntu..
XZ Backdoor: A Highly Technical Attack
In addition to the highly elaborate social engineering discussed earlier in this article, the backdoor itself is very complex.
Senior Threat Researcher at Microsoft Thomas Roccia designed and published an infographic to show the entire operation leading to CVE-2024-3094 (Figure A).
Figure A
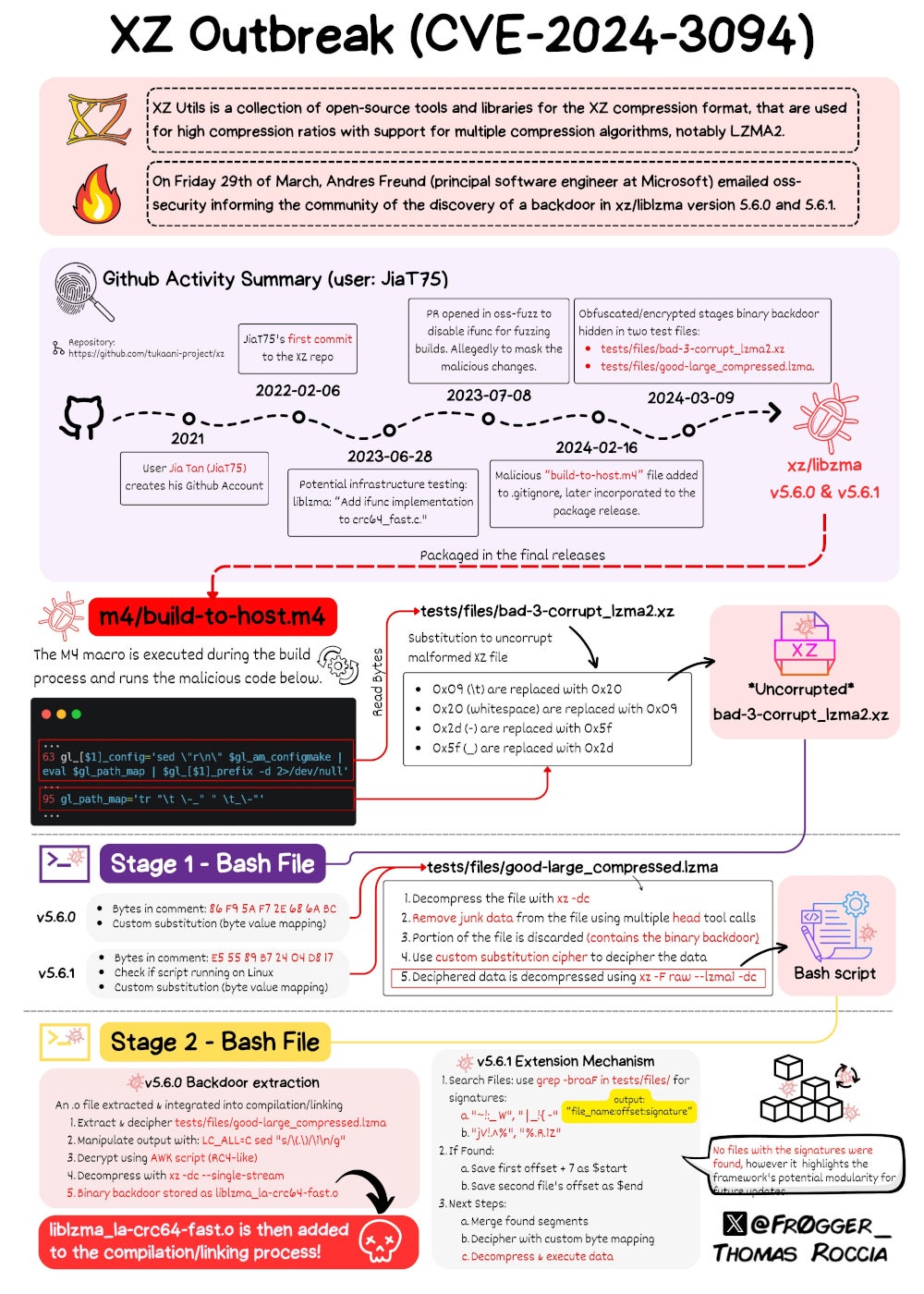
The backdoor is made up of several parts that have been included in multiple commits on XZ Utils GitHub, described in depth by Freund.
Gynvael Coldwind, CEO of HexArcana Cybersecurity GmbH, a cybersecurity company that offers consulting services and courses, wrote A detailed analysis of the back door states that “someone put a lot of effort into making it look fairly innocent and decently hidden. From binary test files used to store payload to file carving, substitution ciphers and an RC4 variant implemented in AWK, all done with standard command line tools. And all this in 3 stages of execution, and with an 'extension' system to future-proof things and not have to change test binaries again.”
DOWNLOAD: TechRepublic Premium Quick Open Source Glossary
Martin Zugec, director of technical solutions at Bitdefender, said in a statement provided to TechRepublic that “this appears to be a meticulously planned, multi-year attack, possibly backed by a state actor. Considering the enormous efforts invested and the low prevalence of vulnerable systems we are seeing, the threat actors responsible must be extremely unhappy right now that their new weapon was discovered before it could be widely deployed.”
What operating systems are affected by the XZ backdoor?
Thanks to Freund's discovery, the attack was stopped before it spread on a larger scale. Cybersecurity company Tenable exposed the following operating systems known to be affected by the XZ backdoor:
- Rawhide fedora.
- Fedora 40 Beta.
- Fedor41.
- Debian testing, unstable and experimental distributions versions 5.5.1alpha-01 to 5.6.1-1.
- openSUSE Tumbleweed.
- openSUSE MicroOS.
- KaliLinux.
- Linux Arch.
In a blog post, Red Hat reported that no versions of Red Hat Enterprise Linux are affected by CVE-2024-3094.
Debian indicated that no stable version of the distribution is affectedand Ubuntu posted that no released version of Ubuntu was affected.
The MacOS homebrew package manager rolled back XZ from 5.6.x to 5.4.6, an older but safer version. Bo Anderson, maintainer and member of the Homebrew technical steering committee, declared that Homebrew doesn't “…believe that Homebrew builds were compromised (the backdoor only applied to deb and rpm builds) but 5.6.x is being treated as no longer trusted and as a precaution we are forcing the downgrade to 5.4.6”.
How to mitigate and protect yourself from this XZ backdoor threat
More systems may be affected, especially those on which developers compiled vulnerable versions of XZ. Security company Binarly offers an online detection tool which could be used to test systems to see if they are affected by the XZ backdoor.
The XZ version should be checked carefully, as versions 5.6.0 and 5.6.1 contain the backdoor. It is recommended to roll back to a previously known secure version of XZ Utils, such as 5.4.
Software supply chain attacks are increasing
As previously reported on TechRepublic, threat actors are increasingly using software supply chain attacks.
However, common software supply chain attacks primarily consist of successfully compromising a key account in the software development process and using the account to send malicious content to legitimate software, which is often detected quite quickly. In the case of XZ Utils, it is very different because the threat actor carefully managed to gain the trust of legitimate developers and become one of the maintainers of the tool, allowing him to slowly introduce different vulnerable parts of the code into the software. Without anyone noticing.
Software supply chain attacks are not the only growing threats; Other supply chain attacks based on IT products are also increasing.
Therefore, companies must ensure that third parties are taken into account when monitoring the attack surface.
Divulgation: I work for Trend Micro, but the opinions expressed in this article are my own.









