Two new vulnerabilities affect ConnectWise ScreenConnect, the remote desktop and access software used for support: CVE-2024-1709 and CVE-2024-1708, with the former being particularly dangerous for organizations.
CVE-2024-1709, affecting ScreenConnect 23.9.7 and earlier, allows any remote attacker to bypass authentication to delete the ScreenConnect user database and gain control of an administrator user. Massive exploitation by attackers continues in the wild, with more than 3,000 vulnerable instances accessible from the Internet. Security companies have observed ransomware, information stealers, and Cobalt Strike payloads, to name a few, being installed after successfully exploiting the vulnerability.
The CVE-2024-1708 vulnerability, which is not as severe as CVE-2024-1709, allows path traversal, allowing an attacker to access files and directories that should not be accessible.
Technical details about the ScreenConnect vulnerability CVE-2024-1709
American cybersecurity company Huntress released technical details on ScreenConnect vulnerabilities CVE-2024-1708 and CVE-2024-1709the latter being particularly dangerous because a simple request to a special route on exposed instances allows an attacker to connect to the instance configuration wizard (Figure A).
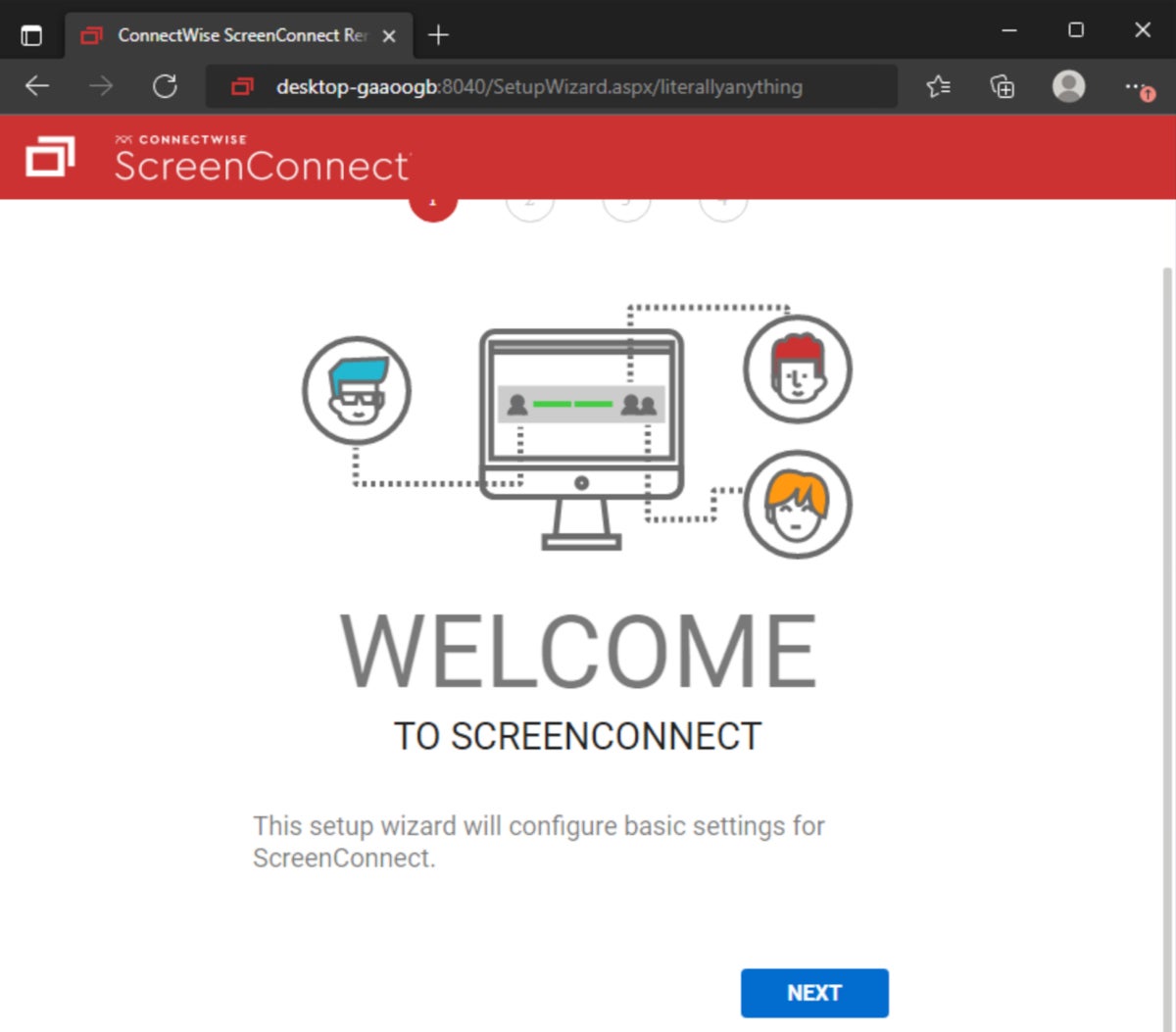
As the Huntress researchers explained, the setup wizard is responsible for setting up the initial administrator user and installing a license on the system. The Huntress team wrote: “The user creation portion of this setup occurs immediately after clicking the 'Next' button on the setup page, so there is no need to complete the entire setup wizard to exploit the system”. If an attacker completes this step, the internal user database will be completely overwritten and all local users will be deleted, leaving only the attacker as the administrator of the instance.
Once this is done, it is trivial to create and load a malicious ScreenConnect extension to obtain full remote code execution on the instance, according to the researchers.
Another vulnerability, CVE-2024-1708, has also been reported, which is a less serious vulnerability that allows path traversal.
Mass exploitation of CVE-2024-1709 in the wild has begun
A proof of concept to exploit CVE-2024-1709 was posted on GitHub, showing how to add a new user to the compromised system.
Cybersecurity company Sophos observed several attacks on February 21, 2024, in which attackers released ransomware created with the LockBit Builder tool in 30 customer networks. Important note: Using the LockBit ransomware creation tool does not mean you have ties to the LockBit developers, especially when the LockBit infrastructure was recently removed. Any cybercriminal with access to the builder can be behind those attacks, and the ransom note observed by Sophos mentioned the “buthtiRansom” variant. Sophos stated that another ransomware based on the LockBit builder called “LockBit Black” was observed but was not deployed in the customer's environment.
Cobalt Strike Password Stealers, RATs, and Payloads
Cybersecurity attacks other than ransomware are currently affecting exposed vulnerable instances of ScreenConnect; For example, password stealers (such as Vidar/Redline) or RATs (such as AsyncRAT) have also been observed following the exploitation of the CVE-2024-1709 vulnerability.
Cobalt Strike payloads have also affected exposed ScreenConnect instances. Sophos saw three similar attacks that dropped a .cmd file in the temporary folder where ScreenConnect downloads files before executing it. The cmd attempted to start PowerShell to download an additional payload, but failed due to endpoint protection.
Thousands of ScreenConnect instances exposed, mostly on US IP addresses
ONYPHE, a French cyber defense search engine dedicated to the discovery and management of attack surfaces, provided TechRepublic with statistics on exposed ScreenConnect instances.
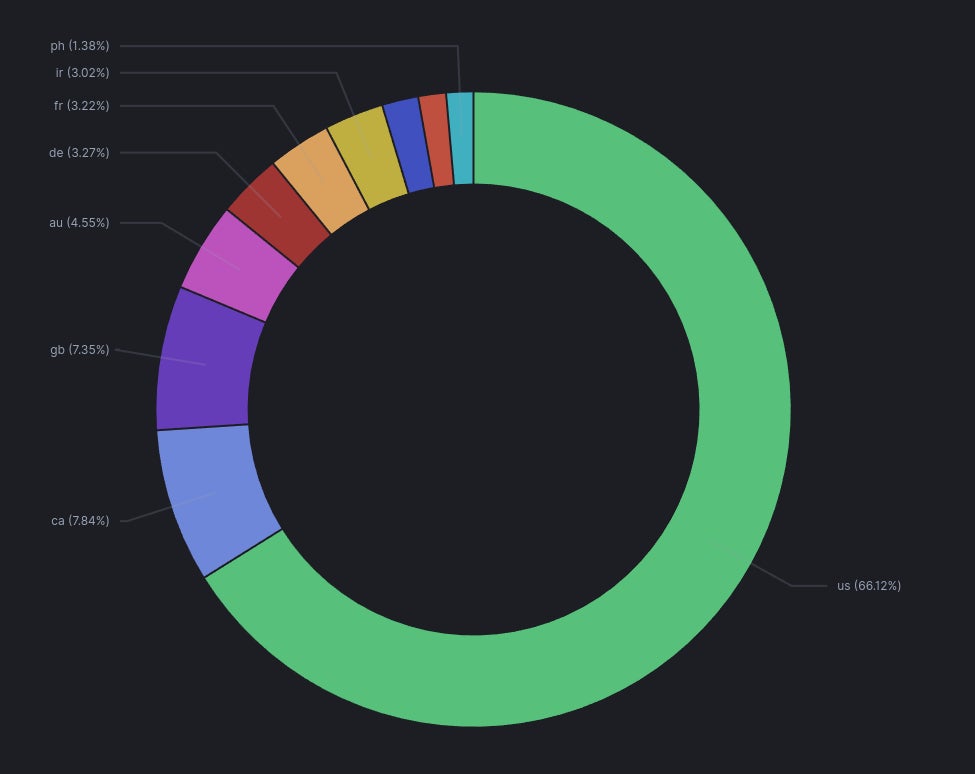
Between February 19 and February 25, 2024, ONYPHE saw 5,731 unique ScreenConnect IP addresses exposed, of which 3,284 were vulnerable to CVE-2024-1709. The majority of those instances are running on US IP addresses (66.12%), followed by Canada (7.84%) and the UK (7.35%).Figure B).
How to Protect Yourself from Exploitation Through These ConnectWise ScreenConnect Vulnerabilities
How to detect exploitation of these ConnectWise ScreenConnect vulnerabilities
In terms of detection, searching for the pattern “/SetupWizard.aspx/” in the server logs may indicate an attempted attack. The “%ProgramFiles(x86)%\ScreenConnect\App_Extensions” folder should also be monitored as it could be used to store and execute attacker payloads.
SEE: Download this TechRepublic Premium Incident Reporting and Response Procedures Policy
How to Protect Your Business from These ConnectWise ScreenConnect Exploits
ConnectWise indicates this in its security bulletin on February 23, 2024 that they “have taken an exceptional step to support partners who are no longer under maintenance by making them eligible to install version 22.4 at no additional cost, which will address CVE-2024-1709.”
ConnectWise recommends local partners immediately update ScreenConnect to 23.9.8 or higher to address reported vulnerabilities. ConnectWise has also implemented an additional mitigation step for unpatched local users that suspends an instance if it is not on version 23.9.8 or later.
Cloud partners receive remedial action against vulnerabilities reported by ConnectWise. Local partners are recommended to immediately upgrade to the latest version of ScreenConnect. ConnectWise has removed licensing restrictions, so partners who are no longer supported can upgrade to the latest version of ScreenConnect.
Divulgation: I work for Trend Micro, but the opinions expressed in this article are my own.









